In the digital era, devices can share information faster and more efficiently. You can also have several devices connecting to one network, allowing you to download and upload data simultaneously.
Using a hotspot requires cellular data to create a network from your phone to other devices, especially outdoors.
However, the security of your network is equally important to avoid malware or leaking crucial information to hackers. The network security key protects your wireless network, including a hotspot, by limiting devices connecting to your network.
CONTENTS
What is a Network Security Key?
A network security key is a password to your network, allowing devices to connect to your hotspot network. The term “password” can replace the network security key since it is common to see its use in many devices.
Therefore, without the key or password, you cannot access a network, whether it is a Wi-Fi network or a hotspot.
Each hotspot’s network security key is unique since it comprises different characters and numbers. Nowadays, biometric data and digital passphrases or signatures are in use in place of characters and numbers for the password.
Thus, it would be best if you had the right combination and use it as a password to connect to the hotspot device. Biometric data, such as fingerprints, offer more secure passwords since they are distinct and unique.
The key is mainly in place to ensure a secure connection between the connecting devices and the hotspot. Therefore, if you use your mobile phone as a hotspot, you will limit the number of devices connecting to your network.
Securing your network by limiting the devices reduces the chances of receiving malware from online hackers. The hackers will extract your personal data and use it for ill motives, such as extortion.
If your hotspot network is not secure, unauthorized users might send spam emails and use them for phishing. The scammer will use fraudulent means to obtain your personal and confidential data, mainly found on your phone.
Types of Network Security Keys in a Hotspot Network
There are three main types of network security keys that you can use for your hotspot. The security keys vary mainly due to the type of encryption they use.
They are:
1. Wired Equivalent Privacy (WEP)
WEP is the earliest form of security code, mainly found in older devices. It is obsolete since it is not very secure, and hackers can easily break into your network using decryption software.
It offers very little protection since it uses static encryption codes for encrypting data between the host device and clients. Therefore, anyone can quickly obtain information from devices connecting to the hotspot network.
WEP Explained
2. Wi-Fi Protected Access (WPA)
WPA relies on dynamic encryption codes to secure data within the network. It uses a unique key whenever data is sent at any point within the network.
Additionally, it uses a Temporal Key Integrity Protocol (TKIP), which performs integrity checks, making it harder to intercept data. Therefore, it is more secure and protects your hotspot network from malware, such as viruses.
WPA and WPA2 Explained
3. Wi-Fi Protected Access 2 (WPA2)
WPA 2 has more upgrades to the WPA key, using an Advanced Encryption Standard (AES) algorithm to secure your data. It also uses dynamic encryption codes and the TKIP function, offering a more secure network.
Additionally, it uses another security protocol for authentication purposes: pre-shared key authentication (PSK). WPA2-PSK is primarily common in recent mobile phone models; hence, your hotspot becomes very secure.
Moreover, there is a WPA3 version found in the latest high-end mobile phones that offers even better data encryption. Therefore, your network is even more secure, even if your set password may be weaker than average.
The network security keys offer different security levels to your network since they may use different encryption methods. It is essential to pick the latest type of key in your device, the most common being WPA2.
Therefore, your data will remain safe from hackers even as you generate your password for your network. Also, you can use more ways to improve your network protection by strengthening your password:
- Use a mixture of numbers and characters if you cannot use biometric data and digital signatures
- Use longer passwords with 8 to 10 characters
- Use a password generator that offers you a unique set of characters for your network
- Use different passwords for your other personal information
- Use a strong VPN application for further data encryption of your network
- Change your password regularly
- Avoid using common names or numbers for your password
Following these tips will increase your hotspot network security, making it harder to hack.
Network Security Key Types Explained
How to Access the Network Security Key on Your Hotspot Device?
You can use different devices to create an internet connection through a hotspot. From your mobile phone to your laptop, the hotspot feature is usually readily available on your device.
However, for your computer, you will share your Wi-Fi connection, while mobile phones use cellular data to establish an internet connection. Also, you can use a hotspot software to manage your hotspot on a computer if it lacks the built-in feature.
You can access your security key settings on the following devices:
On Your Android Phone
- Go to the Settings menu of your phone and select the Connections option according to your device
- Then, select the Mobile Hotspot and Tethering option
- Select Mobile Hotspot to access network security key settings
- Adjust the password, network name, and security according to your preference
How to Create and Personalize a Hotspot on an Android Device (Samsung)
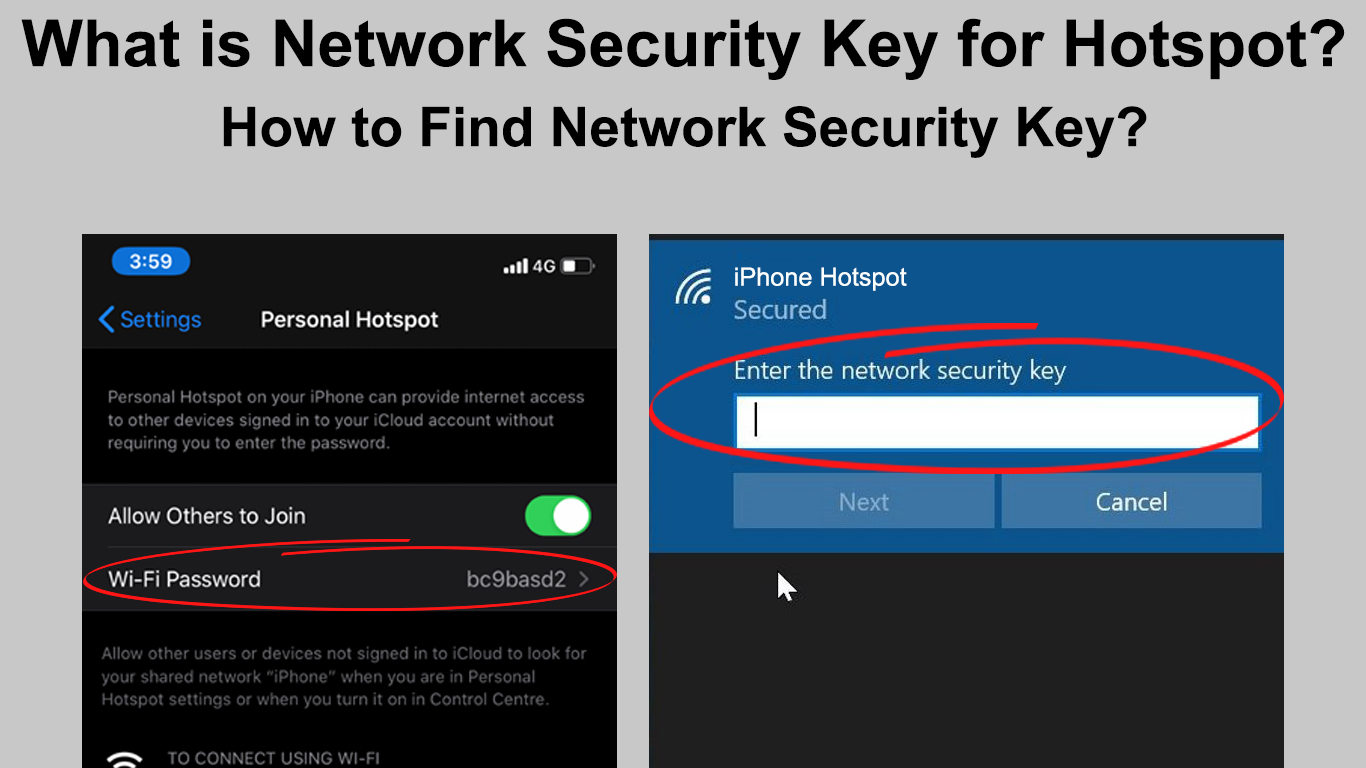
On Your iPhone or iPad
- Go to Settings and select the iCloud option
- Then select the Keychain option and toggle it on to help save your passwords on the devices you approve
- Go back to the Settings menu, then select Personal Hotspots and toggle it on
- You will see your Wi-Fi password from the option
- If the password is not visible, connect your Mac to the Personal Hotspots of your iPhone
- Search for Keychain Access on your Mac and click Enter
- Please type the name of your network and double-click on it
- Enter the admin password of your Mac and check the box on Show Password to get your network’s password
On Your Computer Running on Windows 10
- Go to the Settings menu and select Network and Internet
- From the Status window, select the Change adapter option found below the Change your network settings menu
- A Network Connections window will pop up, where you will right-click on your active network adapter
- Select Status and then select the Wireless Properties option
- From the window, select Security, then the Network security key option
- Select Show characters to reveal your network security key
How to See Your Network Security Key in Windows
On Your Mac
- Open your Finder and select Go
- Then, select Utilities and click on the Keychain Access option
- Login and scroll to find your active network connection
- If it is not available, select the Systems option to find it there
- For Mac OS older than version 10.6.x, select the All Items option from the Keychains window for your active network
- From the Attributes option, select and check the box on Show password
- Enter your Mac admin password and click OK
- You will then find your network security key
Conclusion
When setting up a hotspot, you will need a network security key or password to secure your network. The security key permits only a few devices to connect to your hotspot network.
Therefore, you can protect data in your device and other devices connecting to your mobile hotspot from hackers. The better your encryption code in your network, the safer your data will be.
You can obtain the network security key from your device using the steps shown above. Having a stronger password ensures better security to your hotspot network so make sure to create a strong one.

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.