It’s obvious from your search that there’s an application that’s bothering you or causing issues and you’d like to block it. Unfortunately, you have trouble understanding how to block a program in Firewall in Windows 10.
We’re going to show you how you can do it, and we’re going to squeeze in a little info on what a firewall is and how it works. After reading this, you’ll know a lot more about firewalls and how to use them.
CONTENTS
What Is a Firewall?
It has an illustrious name, and it’s a brilliant and essential feature of every sophisticated piece of hardware. Routers, servers, computers, laptops, gateways, smart devices, etc., all should have a built-in firewall.
It’s a system, a filter that separates the good from the bad. As we are connected now more than ever, and we take connection lightly, we can say that the firewall is a necessary component. Essentially, it is a shield for our devices.
How Does a Firewall Work?
There are four features every firewall should have to make it the most secure one. Although, there are firewalls that work with one of these features, with a combination of these features, and with all four:
- Packet IP filtering: If there were previously identified threats coming from a certain IP address and the packets have that IP address, the firewall will prevent them from entering our device and leaving our device if they’re coming from us.
- Stateful inspection: If there are packets that are not part of a legitimate connection, they will be removed or prevented to enter our network. The firewall scans the data packet headers to determine if the connection is legitimate.
- Proxy service: A firewall mirrors the device that’s connecting to the network, and there’s no direct connection with the device. It protects your location from malicious attackers and malicious code.
- Deep packet inspection: Before you receive or send any data packets from your device, your firewall can decrypt and encrypt them to identify any present malicious code inside the packets before they reach their destination.
Firewall Explained
Types of Attack on Firewall
There are several types of attacks that can occur without us even knowing because we have a great firewall in place. These attacks include DoS attacks, backdoor attacks, remote attacks, spam, viruses, etc.
1. DoS
DoS (Denial of Service) attacks should shut down a service or a machine running that service so that other users can’t access it. A denial of service attack is very convenient, and it’s easy to pull off.
The targeted server holding the service (providing it) is flooded with activity(traffic). It’s overloaded, and it shuts down because that’s the next logical thing to do. The service becomes unavailable for some time.
DoS Attacks Explained
2. Backdoor Attacks
When a backdoor attack is performed, a part of the security strategy is bypassed. For example, you have a password or username that’s the standard credential in any security protocol. With a backdoor attack, these credentials are bypassed. The attacker gains access to your device.
What is a Backdoor Attack?
3. Remote Login
This is exactly what the name suggests. A remote login attack means that someone will control your device as if you were the one doing all the actions. Controlling your device remotely from some other device can be quite handy. It’s a good and useful option.
However, hackers can access the data you may deem sensitive. They can even start unwanted app installation or do some severe damage to your storage.
4. Spam
You’ve probably come across many spam messages in your email inbox. This is what a firewall can do for you. It can protect you from malicious spam mail. Attackers can be tenacious; they won’t stop until they get what they want, and that’s where spam comes in. But our firewall is usually stronger than spam.
5. Macros
If you’ve been using Excel for a while, you probably know what a macro is. It’s a set of rules and processes integrated into one procedure. You can run it easily by clicking on a button. Well, a macro attack relies heavily on macros.
Now, hackers are crafty, and they know how to make macros probably better than most people that use or have used Excel. So, they can easily perform an attack on our device and integrate these macros to perform some serious processes.
6. Viruses
Viruses can replicate themselves as they represent small programs that spread across networks. Of course, every computer virus has to have a creator. So, they are created by a human hand, but they can easily distribute and replicate to all the devices within a network.
Windows Defender Firewall
The Windows Defender Firewall has a few significant features. It’s also called the Windows Defender Firewall with Advanced Security. With its layered security, the data is filtered when entering and exiting the network.
Also, the Network Location Awareness feature assigns firewall settings according to the type of network you’re visiting. Finally, the firewall isolates your network from the internet and other private networks where you can control familiar and unfamiliar network traffic.
Introduction to Windows Firewall
Windows Defender Firewall Best Practices
Like with every other type of software, there are some things we should adhere to. Best practices tell us which good thing other people did to make the software work well. Here, there are a few things you should know about the Windows Defender Firewall:
- Default is good: Sometimes it’s best to keep the default settings. Here, Microsoft did a good job, as the defaults provide a thorough security approach for your device, and you have almost nothing to worry about.
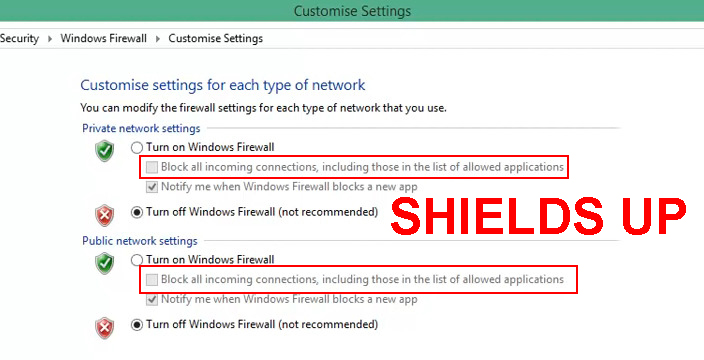
- Learn about “Shields Up”: If you know that you’re in the middle of an attack, e.g. you notice that something strange is happening in the background while you’re on your device, you can always use the “Shields up” feature to block all connections.
- Create outbound rules: In large organizations, it’s necessary to create outbound rules for enterprise applications. These apps are designed for a specific use, so network administrators must handle the regulations to govern the way these apps connect to a network.
- Create application rules: It’s best to create a rule that scans an application before the first launch or even before the installation. You’ve probably seen the pop-up warning that asks you if you’re sure about installing something. This is one filter of your firewall.
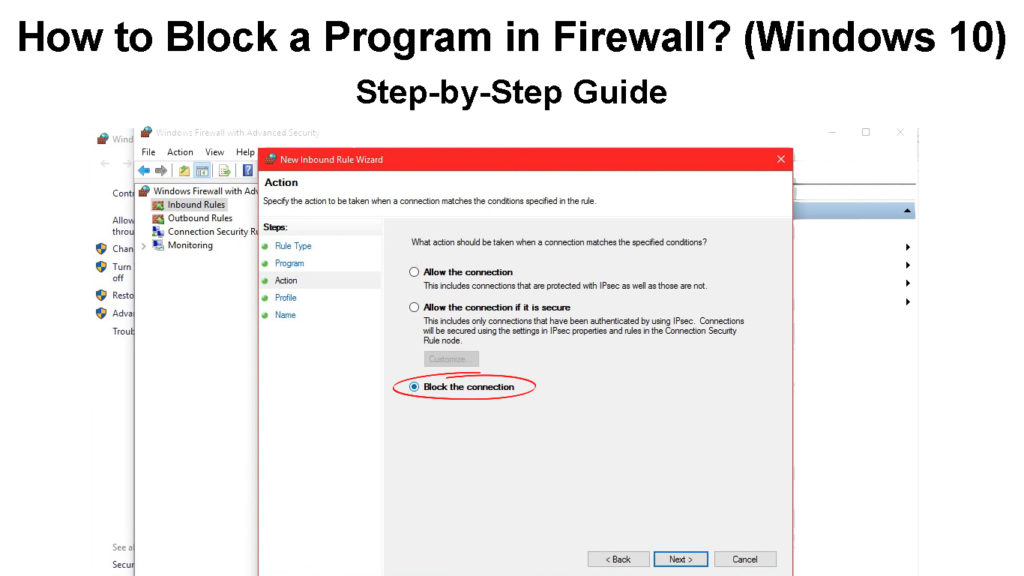
How to Block a Program in Firewall?
Now that you know the features and the protection a firewall can provide, we can learn how to block a program in Firewall. The attacks that we mentioned can’t happen when you know the specific program to block:
- Click on the Search box and type Windows Firewall. Click on the first result.
- When you open it, click on Advanced settings on the left pane.
- Next, click on the Outbound rules section.
- Click on New rule on the right pane.
- Once a new window appears, select Program.
- Then, find the .exe file in the This program path line.
- Click Next and give this rule a name.
- Finally, click on Finish and you’re done.
This way, you have blocked a program from accessing the internet through Windows Firewall.
Blocking a Program Using Windows Firewall (Windows 10)
Conclusion
Learning how to block a program in a firewall (Windows 10) is not that difficult. It takes just a few simple steps. Remember, a firewall is an essential layer of protection for our device and no sophisticated device should work without it.

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.
