We all use the internet every day for all kinds of things without even thinking about how it all works. You just click a button, and the mail is sent. Within a few seconds, on the other end, the mail is received. It’s all so quick and simple. We can all agree it’s quick. But is it really that simple? Have you ever wondered what happens behind the scenes that makes networking so smooth and simple? The backbone of networking is the so-called TCP/IP model, and that will be our main topic today.
In this post, we will explain the purpose of the TCP/IP model and try to describe how it works.
CONTENTS
What Is TCP/IP Model?
Networks work correctly because all devices and software follow a certain set of rules, coming in the form of standards and protocols. Today, the most used networking model is TCP/IP. Every device that’s supposed to connect to the internet made today features support for TCP/IP.
Every Windows PC supports TCP/IP Protocol (as well as every macOS computer, every iOS device, every Android device, et.)
TCP/IP is a model used to standardize computer networking. It defines the way computers communicate on a network. The TCP/IP model consists of a few layers. Each bit of data sent from one computer to another has to pass through all those layers before being sent and/or received.
What Does TCP in TCP/IP Stand For?
TCP is an abbreviation for Transmission Control Protocol. It is a communications standard that enables sending packets over the internet and ensures that the packets are successfully received on the other end.
TCP defines the way the application data is sent from one computer over the internet to another computer or server. TCP splits data into smaller bits called segments before sending them. For every segment sent, the TCP protocol creates a header with some basic information about that segment.
The header includes information about the source and destination ports. The application used for communication between devices determines the port number. For example, if the application is HTTP (if you’re trying to open a website), the destination port will be 80. If you’re trying to visit an HTTPS website, the destination port will be 443. When using an SMTP email server, the destination port will be 25. If you’re trying to transfer files from a server (FTP protocol), the destination port in the header will be 20 and 21.
Assuming that you’re a client communicating with some kind of server, the source ports for your device are randomly generated by the TCP. When you’re visiting a website, you’re a client communicating with the web server (HTTP or HTTPS server). So, when you type in the web address and hit enter, TCP randomly assigns some source port to a specific tab on your web browser. Through this port, your computer will receive the information from the server.
When your request reaches the web server, the server will send the data to you. The data will also have the TCP header with source and destination ports. In this case, the source port will be 80 (HTTP website) or 443 (HTTPS website), and the destination port will be that randomly generated port number by the TCP on your computer. As a result, you will see the content of the website on your browser.
Besides the source and destination ports, the TCP header contains lots of other information.
For example, TCP also assigns a sequence number to each data segment, so that the receiver knows if all the segments have reached the destination and how to put all the segments back together.
Furthermore, acknowledgment numbers are assigned to each segment so that the receiver can tell the sender which packet is expected to be received next.
The checksum is another piece of information found in the TCP header. This info is used for error detection. For each data segment, before sending it, the TCP calculates the checksum for that segment. When that segment reaches the receiver, the receiving machine calculates the checksum as well. If the values match, the data is received. If the checksums don’t match, the receiver will drop the data.
TCP header contains a few more bits of information, but let’s not complicate things too much. This will be more than enough to explain how TCP/IP model works. If you want to learn more about the TCP header, watch the video below.
TCP Header Explained
The point of all this information in the TCP header is to ensure a safe and reliable flow of data from the sender to the receiver.
TCP is not the only protocol used for data transmission. The other common protocol is called UDP or User Datagram Protocol. It’s similar to TCP but much simpler. Each data segment sent using UDP also has a header, but the header is much smaller. It only contains source and destination ports, length, and checksum. UDP is not as reliable and, depending on connection quality, you may lose lots of data packets. TCP, on the other hand, will prevent such occurrences and will resend every lost data packet. So, why do we use UDP if it’s so unreliable?
Well, the truth is – some applications put speed and low-latency communication above reliability. Such applications are voice and video calling, as well as online gaming. For such applications, your computer will always use UDP protocol instead of TCP. Applications that don’t require low latency will always use TCP. So, for example, when trying to upload or download a file from a server, your computer will use the TCP protocol because it’s more reliable and will protect the integrity of your data.
TCP vs. UDP
What Does IP in TCP/IP Stand For?
IP stands for Internet Protocol. It is a set of rules that enables the communication of devices on a network by assigning unique addresses (IP addresses) to each device. There’re two IP protocols – IPv4 and IPv6. IPv4 is currently in use, while IPv6 is not fully implemented yet.
IPv4 defines an IP address as a unique sequence of 32 bits. Each device on a network must have a unique address. Otherwise, it won’t be able to communicate with others.
All IPv4 addresses are divided into 5 classes (A to E), based on the size of the networks they are used on. Furthermore, they are divided into two groups – private and public. Public addresses are used for communication on the internet, while private addresses are used for communication with other devices connected to a LAN network.
All devices in your home have private IP addresses. Your entire home network (all devices in your home) has only one public address assigned to it by your ISP. All devices in your home use that one public IP address to go online, but they use private addresses when communicating with other devices on your home network.
Finally, all IPv4 addresses can be either static or dynamic. Static addresses stay with one device (server, computer, printer, gaming) and don’t change over time – one device will always have the same address. Dynamic addresses change over time.
The purpose of IP addresses in the TCP/IP model is pretty obvious. Without them, our devices couldn’t receive nor send any data because data wouldn’t know where to go.
TCP/IP Layers
As mentioned, the TCP/IP model is a set of rules and protocols that defines how data travels from one computer to another. TCP and IP are the backbones of this model, but there’s a bit more to it.
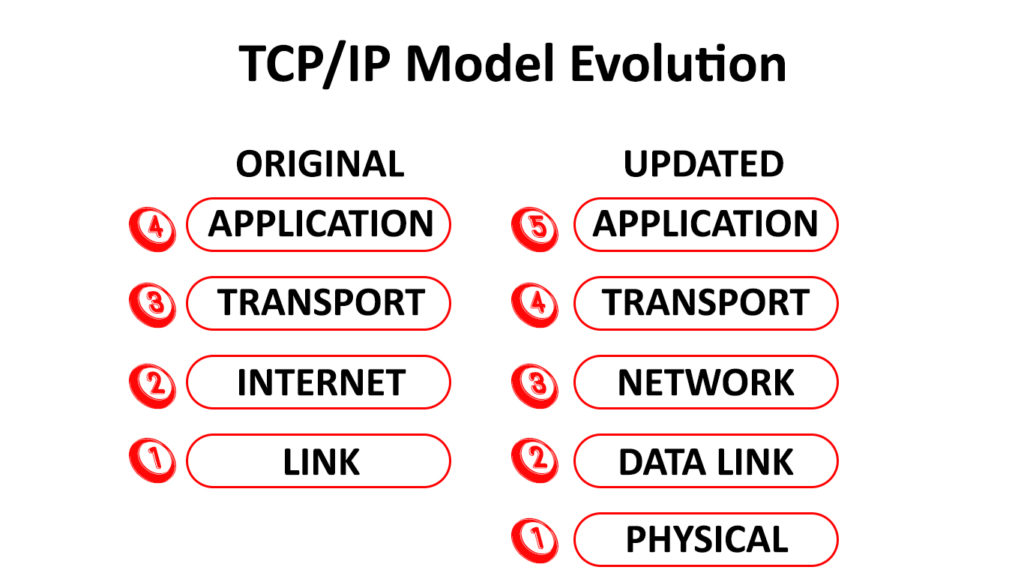
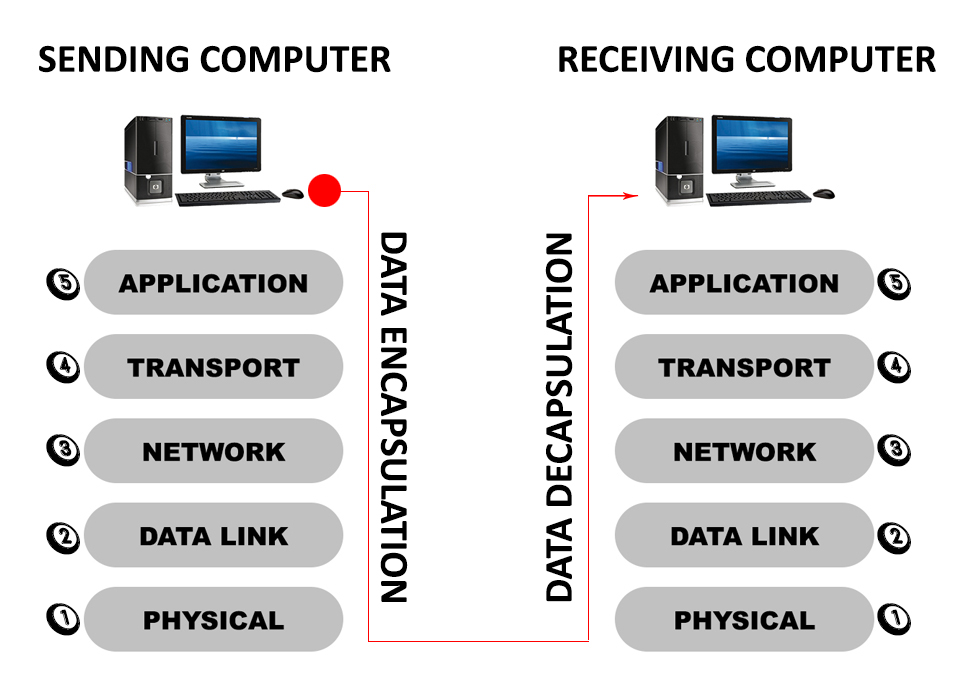
The TCP/IP model used today consists of 5 layers – APPLICATION, TRANSPORT, NETWORK, DATA LINK, and PHYSICAL LAYER.
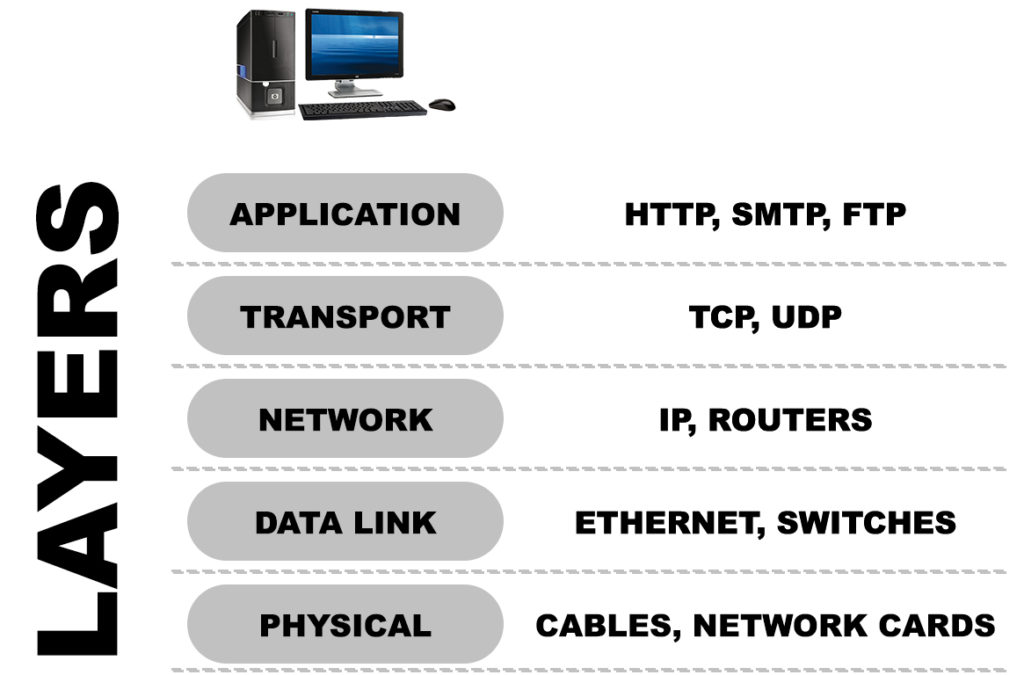
Every bit of information has to pass through all these layers before being sent. It also has to pass all the layers on the receiving end before being received.
The original model consisted of four layers APPLICATION, TRANSPORT, INTERNET, and LINK. The new, updated TCP/IP model renamed the INTERNET LAYER to NETWORK layer, while the LINK layer is divided into two – DATA LINK and PHYSICAL layer. So, instead of 4 original layers, now we have 5 layers.
At each layer, we have different protocols and devices. Each layer will add its own bit of information. The entire process is named encapsulation. Once the data reaches the physical layer, the data is transmitted to the receiving device (whether over the internet or within a much smaller LAN network). The receiving device will then start to decapsulate every packet of data and rearrange them.
How Does TCP/IP Work?
As mentioned, the data has to go through each layer before being sent (encapsulation) and then has to go through each layer on the receiving end before being received (decapsulation). Let’s discuss these two processes.
Data Encapsulation
The topmost layer is called the APPLICATION layer. Programs (like your browser, Skype, or your online games) directly interact with this layer. It all starts with the application data created at this layer. The data could be any file sent from your computer to some other computer. It could also be your request to open a website or a command in a video game. This layer consists of application protocols like HTTP (unsecure websites), HTTPS (secure websites), SMTP (email protocol), FTP (file transfer protocol), Telnet, SSH, etc.
The layer below is the TRANSPORT layer – that’s where the TCP lives, along with UDP. This is where the data gets chopped into small bits of data called SEGMENTS. By segmenting the data, TCP enables much faster transmission and allows each packet to take the quickest route. They may not arrive at the destination in the same order, but that’s why we have TCP headers. Each segment gets a TCP header, as discussed above. Based on the application in the previous layer, TCP defines source and destination ports. To ensure each piece of data reaches its destination and that all the data is received correctly, the TCP will also add all the other information we’ve talked about.
Recommended reading:
- What Are Subnets and Subnet Masks? (A Beginner’s Guide to Subnetting)
- What is QoS (Quality of Service) in Routers?
- What is MAC Address Cloning and When to Use It? (MAC Address Cloning Explained)
After the transportation layer, the data moves down to the NETWORK layer, where the addressing is taking place. That’s where the Internet Protocol lives. At the NETWORK layer, every packet receives the so-called IP header, which contains information about the source and destination IP address. That way, the packet knows where it’s going as well as where it came from. When the segment from the TRANSPORTATION layer reaches the NETWORK layer and receives its IP header, it becomes a PACKET. Routers also operate at the NETWORK layer since they are in charge of IP addressing in LAN networks
Finally, the data reaches the DATA LINK layer. Here, each packet receives not just a header but also a trailer. The header contains the source and destination MAC addresses, while the trailer contains error check information that helps the receiving device to check whether the data has been received correctly. The DATA LINK layer contains Ethernet. Ethernet switches operate at this layer as well. After passing the DATA LINK layer, the PACKET becomes FRAME.
Finally, there’s a PHYSICAL layer that includes everything you can actually touch (excluding routers and switches). Cables and network cards belong to this layer. When the data reaches the physical layer, it gets physically transmitted to the receiving end.
Data Decapsulation
The data is physically transmitted to the destination, and that’s where the decapsulation process starts. At the DATA LINK layer, the destination machine checks every FRAME. It checks the source and destination MAC address. If the destination MAC address matches the destination machine, the DATA LINK layer will push the FRAME further up to the NETWORK layer.
Here, the receiving machine checks the destination IP address. If the packet is meant for that specific computer, it will go further up to the TRANSPORT layer. The TCP header is checked, and if everything is correct, the data is sent to the APPLICATION layer, where it finally gets received.
Final Thoughts
There you have it. Hopefully, now you understand what a TCP/IP model is, what it is used for, and how it works. Stay tuned for more interesting articles about networking!

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.
