With today’s technology and the number of attackers on the internet, terms like DMZ are more important to understand than ever. Understanding this term will help you protect your local network from the public and offer various services online without exposing your sensitive data. So, today you’ll find out what a DMZ is and whether using it is a good idea.
CONTENTS
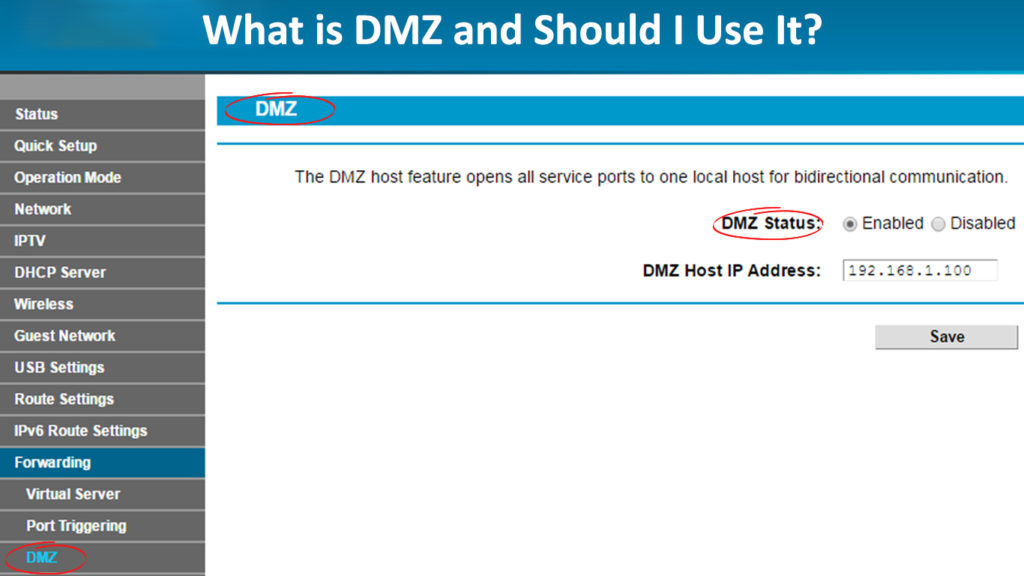
What Does “DMZ” Mean?
DMZ is short for “Demilitarized Zone” and it presents a subnetwork that has the main purpose of protecting the local area network. It achieves that by being a sort of a layer in front of the private network that the public internet can access.
How Does the DMZ Work?
As we mentioned, the DMZ provides an extra layer between the private information on a private local network and the public. The easiest way to explain that is by using a website as an example. Let’s say there is a business that wants to create a website to present to potential clients. This public website has to be accessible from the internet.
However, the fact that it’s public could put the entire internal business network at risk. That is why there are firewalls and other methods of protection in place. If that business chooses too many safety precautions, it could slow down the site’s performance. Thus, it has to choose a selected number of protection methods that will secure the private network without slowing everything down.
That’s where the DMZ comes in. The DMZ is a network where the public servers are hosted and it’s completely separate and isolated from the private part that the business wants to protect. The business could put up a firewall to filter the traffic between the local network and the DMZ.
Furthermore, experts recommend installing another firewall between the public server and the DMZ. That way, everything will stay secure without slowing the site down and affecting the users’ experience.
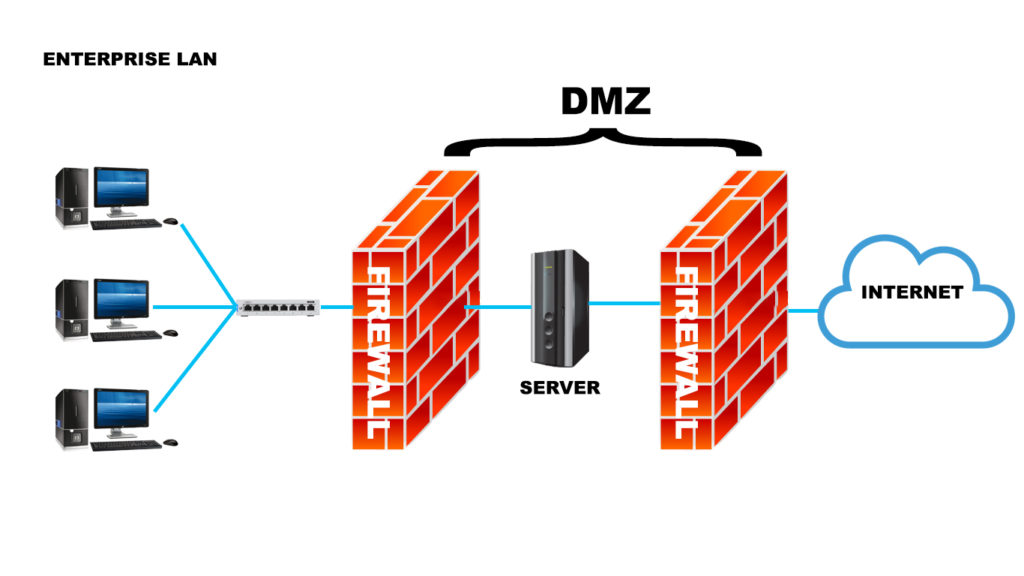
If an attacker would want to access the private local network, they would have to pass through a firewall and the DMZ before getting to the sensitive data. It’s not impossible, but it’s an extremely difficult task, especially because the DMZ has amazing early warning systems that would inform you that there is a potential breach inside the network.
DMZ Explained
The Value of the DMZ
Experts recommend every user that wants to offer services on the public internet to set up the DMZ network. That is why a typical DMZ includes external-facing services and servers such as email, FTP, VIP, DNS, and proxy servers.
Aside from protecting the local network and sensitive data, the DMZ is used for other purposes. For instance, if an organization has to comply with certain state regulations, it’s easier to install a proxy server on the DMZ network. That will make it easier for them to monitor and record the activities of visitors. In addition, the DMZ allows for simpler content filtering and makes sure that employees can use it to access the internet in a more secure way.
The Most Common Uses for the DMZ
As we mentioned, the DMZ is used for many things. But the most common one is the protection from threats. That is why the public servers and services, in general, are usually installed on the DMZ network. If you’re wondering which services should you place on the DMZ, the simple answer is – every service that is supposed to be available on the public web. That is why there are three types of services that are protected by the DMZ more often than not.
1. The FTP Servers
The File Transfer Protocol presents a method of transferring, uploading, and downloading files between devices or various locations on the internet. Since it involves direct interaction with files, owners have to take a few cautionary steps to ensure that the crucial content stays protected. That is why many of the FTP servers are hosted on the DMZ network.
2. The Web Servers
We’ve already explained the importance of the DMZ for web servers. If you have a web server that ensures communication with an internal database, you should try to place it on a DMZ network. That way, your database will remain secure and the information within that database should remain protected.
Even though the DMZ is placed in front of the firewall which means that devices connected to your local area network are protected, experts still recommend installing additional firewalls in front of the server (between the internet and server) as an additional layer of protection (for the server and for your LAN).
3. The Email Servers
When an email server operates inside the DMZ network, users can access the mail database and interact with it without having it exposed to potential malware or outside threats. Emails tend to contain sensitive information and login credentials that have to be protected from the public. That is why they are often placed in the DMZ network. However, the DMZ does not protect it from an internal threat. Thus, it should not be the only way a user protects itself from malware.
Why Should You Use DMZ?
The first and most important reason why using a DMZ is a smart idea is increased security for your LAN network. You’re already familiar with the fact that the DMZ provides controlled access to the outside user. That way, your internal network stays protected without you restricting full access to the public.
The additional layer you have should keep all of your sensitive data out of reach. In case there is a security breach, the DMZ will at least warn you about a potential intrusion, allowing you to prepare for the attack on time.
Other Reasons to Use the DMZ
We’ve mentioned before that the DMZ has other great uses aside from creating an additional layer between the public and your local network. For example, it prevents outside sources from collecting information about the server. Since it’s a buffer between your private info and the internet, the DNZ protects your information from being collected by potential attackers looking for their next target. This process is made even more challenging if you have firewalls installed as additional protection.
What’s more, we’ve already mentioned that many organizations use a proxy server on the DMZ to make monitoring and recording traffic easier. That’s especially useful to businesses that have to abide by state regulations and ensure that every piece of information is up to standards. Furthermore, the control of access is present even without a proxy server as the DMZ is actually controlling the access by remaining between the local network and the internet.
Finally, many users opt for using the DMZ as it prevents IP spoofing. The DMZ is not only a layer that protects your info from being exposed. It’s also another service that’s there to verify the truthfulness of an IP address. Therefore, it will block any spoofing attempt or at least warn you about a potential threat in the process.
Why Would a Regular Internet User Need a DMZ?
If you’re a fan of online gaming, you have probably heard of the DMZ option in router settings. DMZ in routers is not exactly the same thing as DMZ explained above. By enabling DMZ for a certain device (usually a gaming console), you’re designating your console as a DMZ host. What this means in practice is that all router ports will be forwarded to the DMZ host (your console). So, all the traffic that comes to and from your console will not go through your router’s internal firewall.
To make your console a DMZ host, you will have to assign a static IP to it first (or make a DHCP reservation). After that, you can find the DMZ settings, enable them, and enter your console’s IP address as the DMZ server.
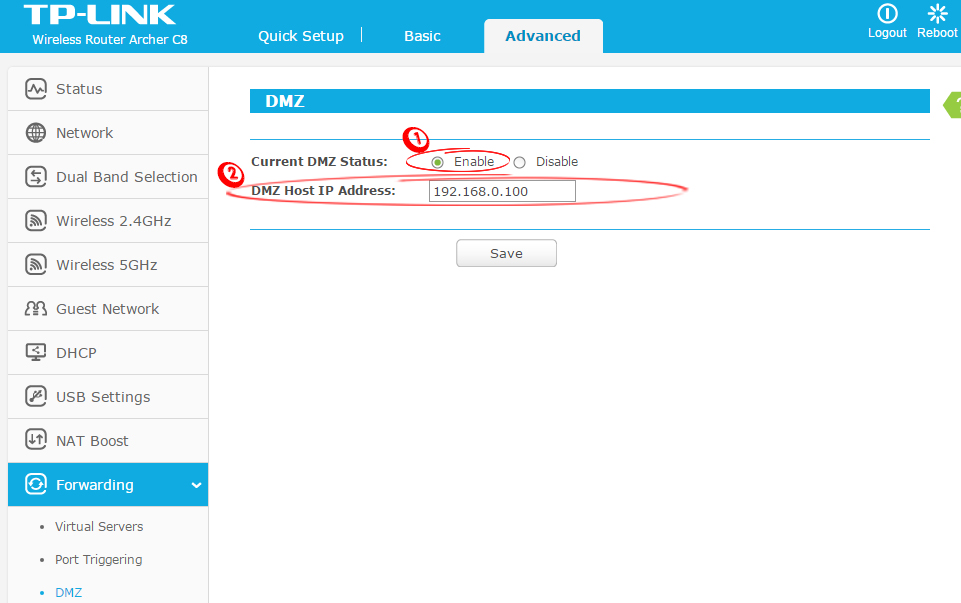
Creating a DMZ host (TP-Link router)
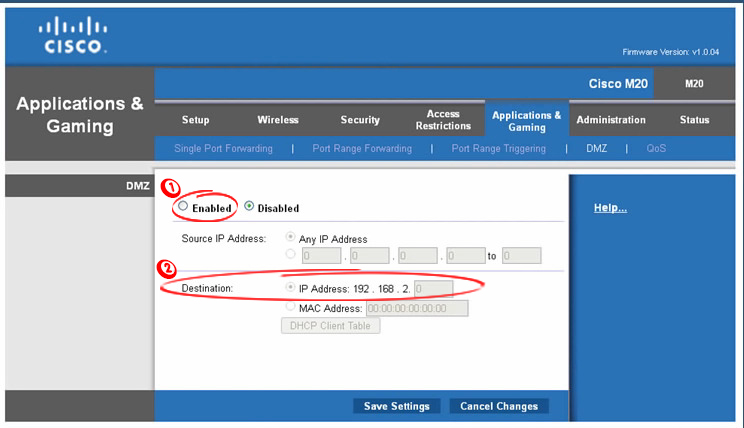
Creating a DMZ Host (Linksys/Cisco router)
The Bottom Line
The DMZ network is extremely useful to anyone that wants to offer services to the public. The internet can be unpredictable and is full of threats. That is why you should do everything in your power to protect your sensitive information from attackers.
The DMZ allows you to have a much less stressful experience with sharing your data. Moreover, if you combine it with firewalls, your local network will stay protected no matter how persistent a potential attacker is!

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.
