For many internet users, mentioning various acronyms and abbreviated IT terms is enough to cause a headache. They couldn’t care less about the terms and functions as long as they could use the computers and other devices online. But sometimes, it is worth knowing some of the main IT acronyms and their functions, especially when you face a problem with your device or internet connection. That brings us to the topic – what is Wi-Fi Protected Access (WPA)?
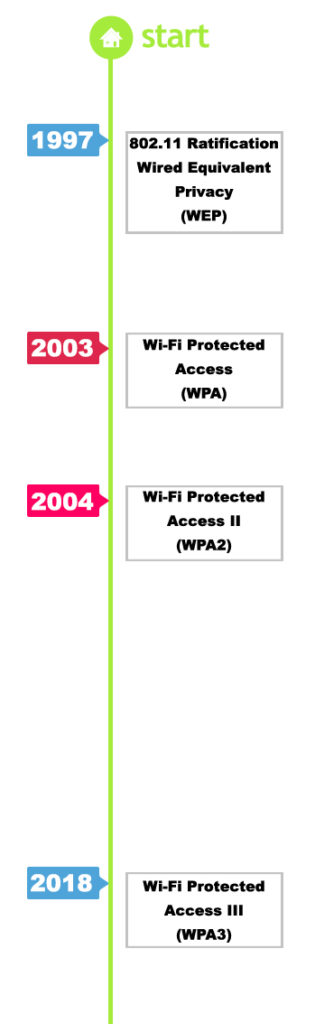
Developed and first released in 2003 by the Wi-Fi Alliance, Wi-Fi Protected Access (WPA) is the standard of security for Wi-Fi-connected devices. The original Wi-Fi security standard is called Wired Equivalent Privacy or WEP. Then, Wi-Fi Alliance developed WPA in an attempt to come up with more advanced data encryption and superior user validation.
The Wi-Fi Alliance created WPA in response to WEP protocol weaknesses. However, WPA was superseded by WPA2 in 2004 to offer a more secure form after a year of the previous version’s release. The current version is WPA3, released recently in 2018, but WPA2 is still widely accepted.
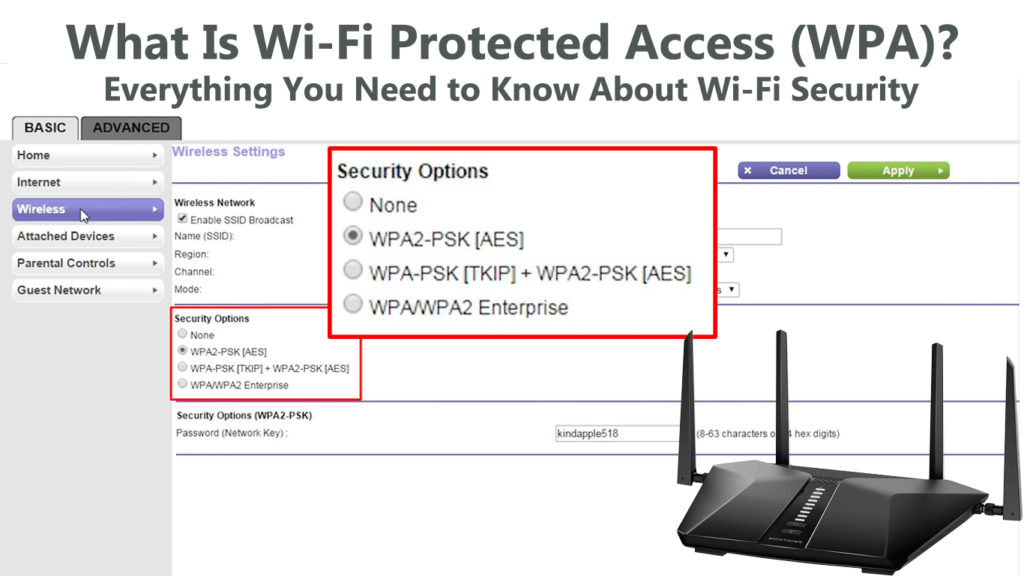
Enterprises and individuals use separate WPA modes. The latest enterprise mode is WPA-EAP, which utilizes a rigid authentication process. Furthermore, corporate users need to communicate with a dedicated server before validating login credentials. On the other hand, the most recent personal mode, WPA-PSK, utilizes SAE (Simultaneous Authentication of Equals) in creating an assured verification.
Let’s take a deeper look into the two versions that are still in use – WPA2, and WPA3.
CONTENTS
WPA2 Protocol
As we already know, WPA2 was established only a year after WPA was first launched. Apparently, there were a lot of things that needed upgrading since the creation of the original WPA version. It operates via the CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol). On the other hand, the original WPA uses the weak and unreliable TKIP (Temporal Key Integrity Protocol). AES (Advanced Encryption Standard), which produces authenticity verification messages, is the basis of the CCMP protocol.
WPA VS WPA2
That said, WPA2 is still vulnerable in some parts, especially where intruders can access the wireless network without any authorization. Hackers can easily attack the wireless network WPS or Wi-Fi Protected Setup access points.
Traditionally, most intrusion threats aim at corporate wireless systems. However, the threats are also common to personal home Wi-Fi systems having weak passwords. In addition, WPA2 also has other weaknesses, such as the one in Transport Layer Security where intruders can attack.
WPA3 Protocol
Despite its weaknesses, WPA2 has been used for a long time. It was the standard protocol since 2004 until WPA3 (Wi-Fi Protected Access 3) superseded it in 2018, though WPA2 is still accepted and widely used to this day. That is a pretty long period for an IT standard to be in use, where many technological advances progress quickly, sometimes in a matter of only a few months.
Today, WPA3 remains the latest standard of WPA implementation. Since it was first implemented in 2018, the Wi-Fi Alliance has been certifying WPA3-compatible products. Most newly launched routers support WPA3, but some manufacturers can update existing routers with WPA2.
Here are some of the updated WPA3 features:
- The encryption of GCMP-256 (Galois Counter Mode Protocol)
- HMAC 384 bit (Hashed Message Authentication Mode)
- BIP-GMAC-256; the 256-bit Broadcast/Multicast Integrity Protocol
- For WPA3-EAP enterprise – 192-bit cryptographic strength
- Simultaneous Authentication of Equals (SAE) exchange
- Provisioning Protocol, DPP for Wi-Fi devices
Inevitably, WPA3 also has its weaknesses, for instance, the five vulnerabilities known as Dragonblood, which consists of a denying-service attack, two attacks to downgrade, and two leaks of side-channel details. The Wi-Fi Alliance has been working hard to overcome such vulnerabilities, which have been appearing from time to time.
WPA3 Explained
Difference Between WPA, WPA2, and WPA3
It’s best to explain the differences between the three WPA standards by looking at how WPA and WPA3 measure up against WPA2.
WPA2 Against WPA
WPA2 has more security features, and it’s much more powerful. We identify some notable differences as follows:
- WPA2 differentiates clearly between individual and corporate modes
- WPA2 uses AES, which is more secure
- WPA2 allows for more immense processing power compared to WPA.
WPA2 is still an acceptable standard if your device is not embedded with WPA3, while the WPA standard is already obsolete.
WPA3 Against WPA2
On the other hand, the latest WPA3 is better secured and more extensive than WPA2. However, the Wi-Fi Alliance has not thrown away the WPA2 standard yet, and many devices still use this standard.
WPA2 features are no match to some of WPA3’s new features, such as the SAE protocol, personalized data encryption, and more robust protection from powerful attacks.
Wi-Fi Password Security Explained
Conclusion
The first version of Wi-Fi Protected Access was announced in 2003, and the Wi-Fi Alliance, being the owner of the Wi-Fi trademark, replaced WEP (Wired Equivalent Privacy) with WPA protocol. Devices were updated to allow WPA implementation, then WPA2 and the latest version WPA3.
WPA has since ceased its validity, but WPA2 is still widely accepted even though Wi-Fi Alliance has already launched WPA3. However, for maximum security, we’d suggest every user obtain WPA-approved devices or update the WPA protocol in existing devices to the latest version – WPA3.

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.
