Wi-Fi is a convenient way of connecting to the internet, especially when most tasks are completed online. When checking into a hotel or any other business premises, it is common for people to use the nearby public Wi-Fi and not cellular data. The preference for Wi-Fi over cellular data is because Wi-Fi is cheaper and faster than cellular data in most cases.
Regardless of the advantages, using Wi-Fi exposes you to risks that can be catastrophic if you do not take the necessary security measures. One such risk is Wi-Fi spoofing, which lets attackers intercept information between your phone and network. Keep reading to understand better Wi-Fi spoofing and how you can protect yourself from such malicious attacks.
CONTENTS
What Is Spoofing?
Spoofing is a phenomenon where someone or a program mimics a legitimate program with malicious intent.
Spoofing is a common tactic that criminals use to access private data that you type into your phone or laptop to be shared over a network. Attackers usually spoof known websites or networks and manipulate victims to enter sensitive information on their devices that the attackers intercept.
Other times the attackers inject malware that grants them access to files on your devices. The malware might also lock you out of your devices, and attackers demand ransom to remove the malware. Attackers usually compliment spoofing with elements of social engineering.
Security Risks of Public Wi-Fi
Social engineering in information security entails the psychological manipulation of people to influence them into divulging confidential information.
If successful, attackers can bypass access controls and end up accessing confidential documents and the network. Suppose the attackers stumble on more passwords stored on your devices; they can wreak havoc, especially since it is not easy to catch properly executed spoofing attacks.
Hacking a Phone Connected to Public Wi-Fi Is Pretty Easy
There are various types of spoofing, as illustrated below.
Types of Spoofing
Email Spoofing
This is the most practiced type of spoofing attack. The attacker forges the email address of a reputable organization by changing a minute detail that is hard to recognize. For instance, they might substitute a zero with the letter O or add an extra letter.
Spoofed emails often contain malware or links to malicious websites that require you to enter, for example, your banking details.
Email Spoofing Explained
https://www.youtube.com/watch?v=rCnz6cfqnWc
ARP Spoofing
The attack entails an attacker linking their device’s MAC address to another device’s legitimate IP address on a LAN.
They do this through the Address Resolution Protocol (ARP), which handles traffic routing within a network.
ARP Spoofing Explained
DNS Spoofing
The attackers interfere with the Domain Name Systems and alter IP addresses to legitimate websites with IP addresses to copycat websites of the original website. It is also called a DNS poisoning attack.
DNS Spoofing Explained
IP Spoofing
In this attack, the perpetrator masks corrupt IP packets with a legitimate source IP. That way, your devices will trust the malicious packets as they appear to come from a legitimate source. The attack is often used alongside DDoS attacks.
IP Spoofing Explained
Other spoofing attacks include; GPS Spoofing, Text message spoofing, caller ID spoofing, and Referer spoofing.
What is Wi-Fi Spoofing?
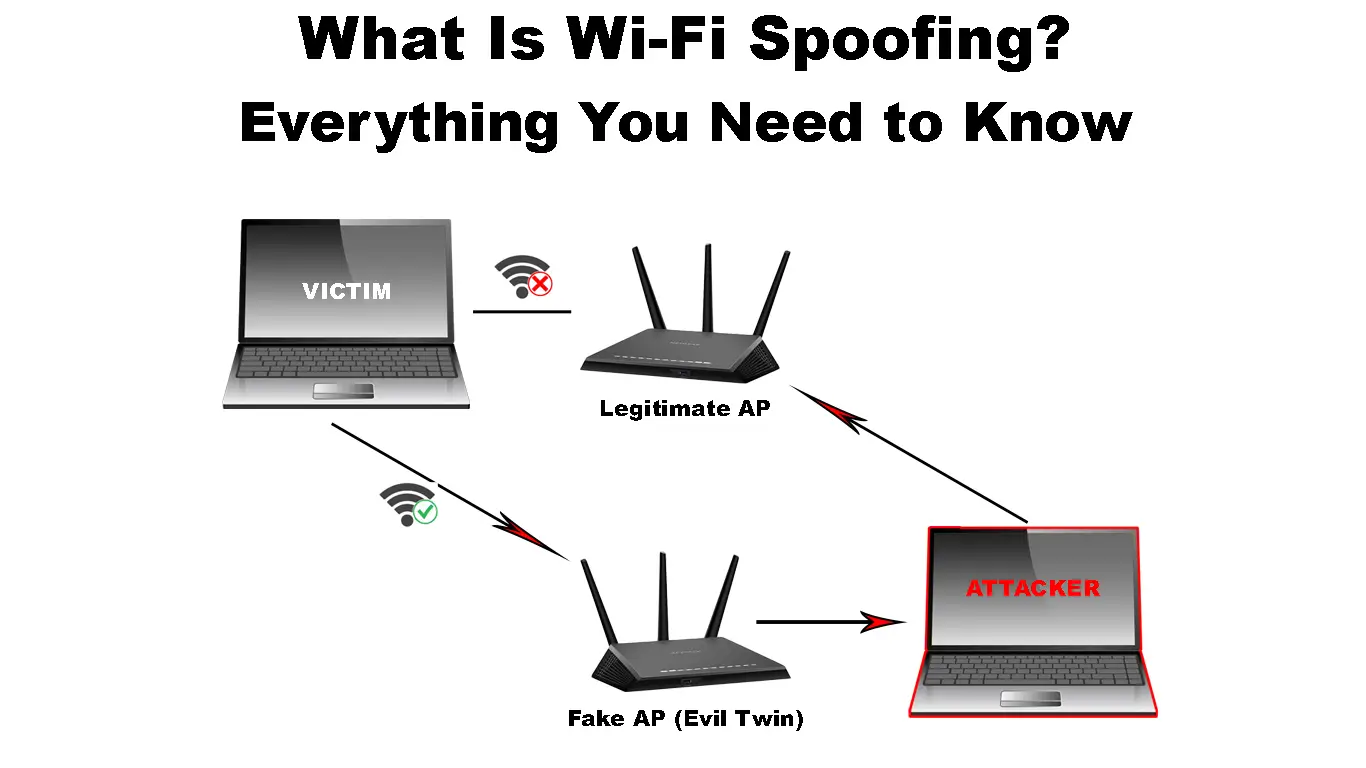
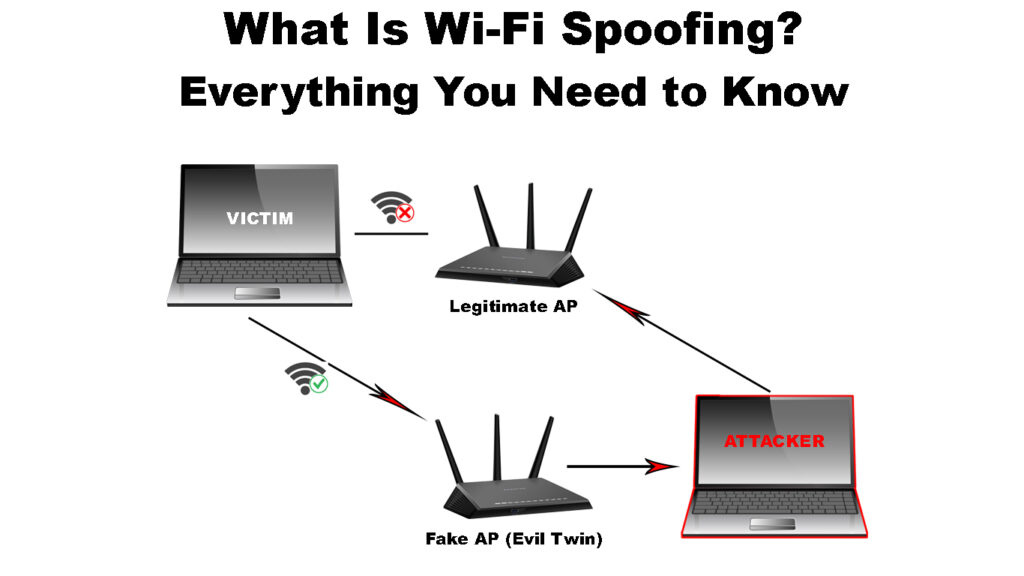
Wi-Fi spoofing is an attack where an attacker mimics a legitimate public Wi-Fi network. Mimicking is done by establishing an SSID similar to the target network’s using a device that can be programmed to act as an access point.
Then when a user connects to the fake network, the attacker can intercept information shared by the user.
The attacker can go the extra mile by setting up a fake captive portal to make the network look as legitimate as possible.
The information the attacker intercepts is; what you type and what is in your shared files.
Attackers can mimic Wi-Fi networks using programs on their devices or devices fashioned for this specific purpose, such as a Raspberry pi or a Wi-Fi pineapple.
The attacker then sets up their malicious network in areas with public networks where someone is more likely to connect to it.
Wi-Fi spoofing is often referred to as an Evil twin attack which entails the attacker setting up a similar network SSID to the one they intend to compromise.
Evil Twin Attack Explained
The attacker then uses a denial-of-service attack to ensure your device does not connect to the legitimate network. After a few tries, the victim is bound to give up and connect to the Evil twin network set by the attacker since it looks similar to the original network.
The victim will be required to enter their network password in the evil network, and the attacker can intercept the password.
In other instances, the attacker might redirect you to a fake login page so they can intercept your router’s admin password and username.
Once the attacker accesses this information, they can use it to access your network at will and modify it as they please. For instance, they can infuse spyware that monitors and redirect your internet traffic to their systems.
Evil twin attacks are often used to gain network credentials such as the Wi-Fi password or the router’s administration login credentials.
How to Avoid Wi-Fi Spoofing/Evil Twin Attacks
Wi-Fi spoofing can be hard to recognize, but if you know it exists, it can be easier to identify. There are a few measures you can take to safeguard yourself from these attacks:
- Avoid public or unsecured networks at all costs. Public networks are never safe as they are easily accessible and have many users making them the best option for anyone wishing to manipulate the network.
- Use a mobile hotspot. If you have to access the internet and cannot use your home Wi-Fi, consider a Wi-Fi hotspot and configure it with a complex password.
- Prevent your devices from automatically connecting to public networks.
- Do not access your private accounts while on a public network. This includes your bank accounts.
- Ensure your systems are up to date. Outdated firmware is easy to manipulate and bypasses any security measures incorporated in the system. Updates are important because they fix vulnerabilities and enhance security using modern protocols.
- Visit secure websites. Ensure the websites you visit have the HTTPS protocol. If a page is not secured, refrain from entering passwords or any personal information on the web page.
- Users can also rely on VPN programs to encrypt their connections, especially if they often use public or unsecured networks.
- Also, use malware protection programs like an antivirus on your devices. They will prevent attackers from installing malicious software into your devices.
- Be keen. Always inspect any networks you wish to connect to. Often malicious networks have slight errors you can notice if you observe intensively. Also, trust your gut when something feels off about a network you wish to use.
Ways to Protect Yourself from Evil Twin Attacks
Conclusion
Technological advances strive to curb spoofing attacks, and there have been significant advances. However, the ultimate responsibility lies with you because criminals are also working on advancing their techniques to evade getting caught.
Avoid connecting to public networks, and if you must be very keen not to connect to spoofed networks. Also, avoid using public networks for vital online services such as bank transactions in case someone else is on the network spying.

Hey, I’m Jeremy Clifford. I hold a bachelor’s degree in information systems, and I’m a certified network specialist. I worked for several internet providers in LA, San Francisco, Sacramento, and Seattle over the past 21 years.
I worked as a customer service operator, field technician, network engineer, and network specialist. During my career in networking, I’ve come across numerous modems, gateways, routers, and other networking hardware. I’ve installed network equipment, fixed it, designed and administrated networks, etc.
Networking is my passion, and I’m eager to share everything I know with you. On this website, you can read my modem and router reviews, as well as various how-to guides designed to help you solve your network problems. I want to liberate you from the fear that most users feel when they have to deal with modem and router settings.
My favorite free-time activities are gaming, movie-watching, and cooking. I also enjoy fishing, although I’m not good at it. What I’m good at is annoying David when we are fishing together. Apparently, you’re not supposed to talk or laugh while fishing – it scares the fishes.